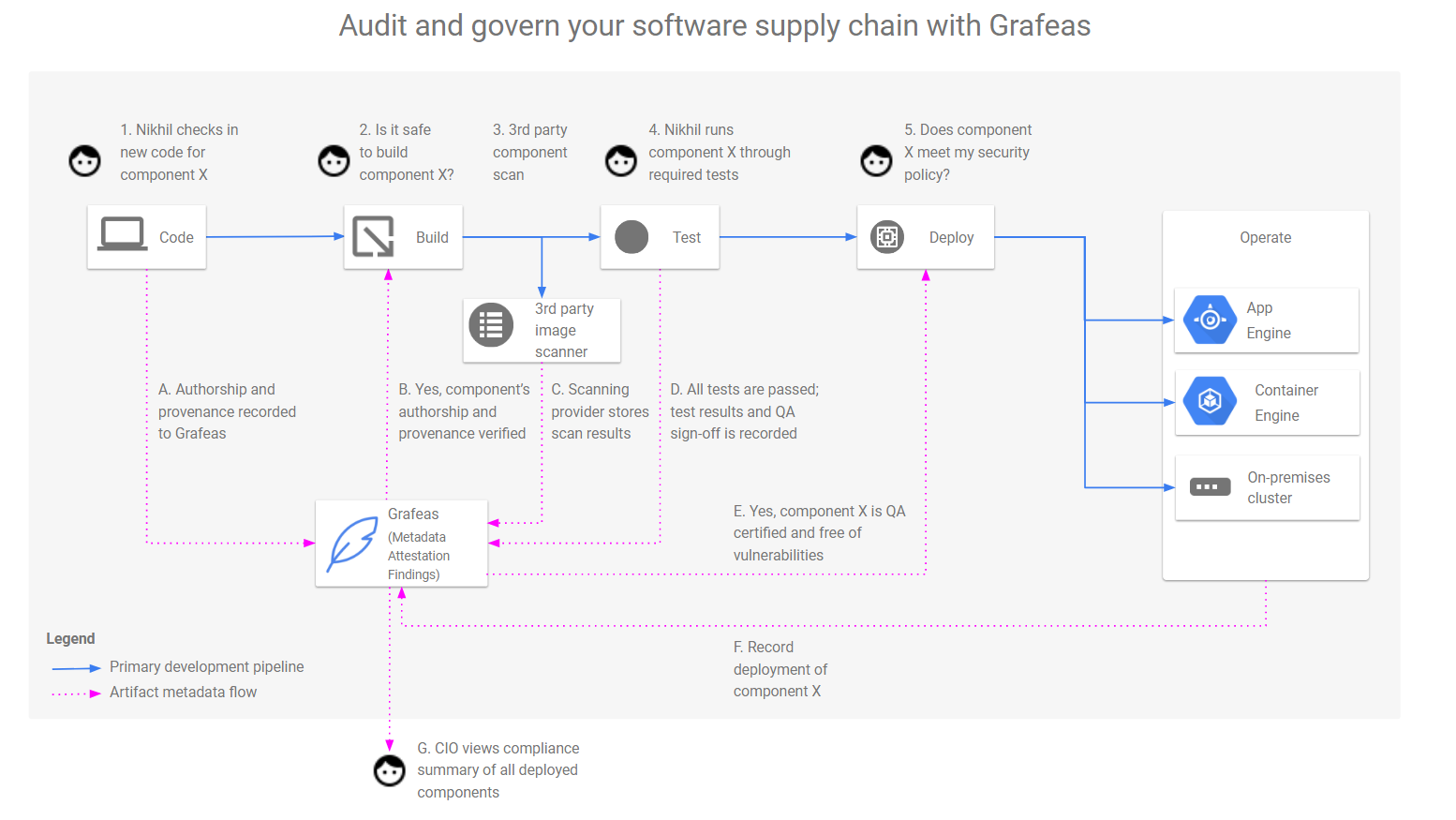
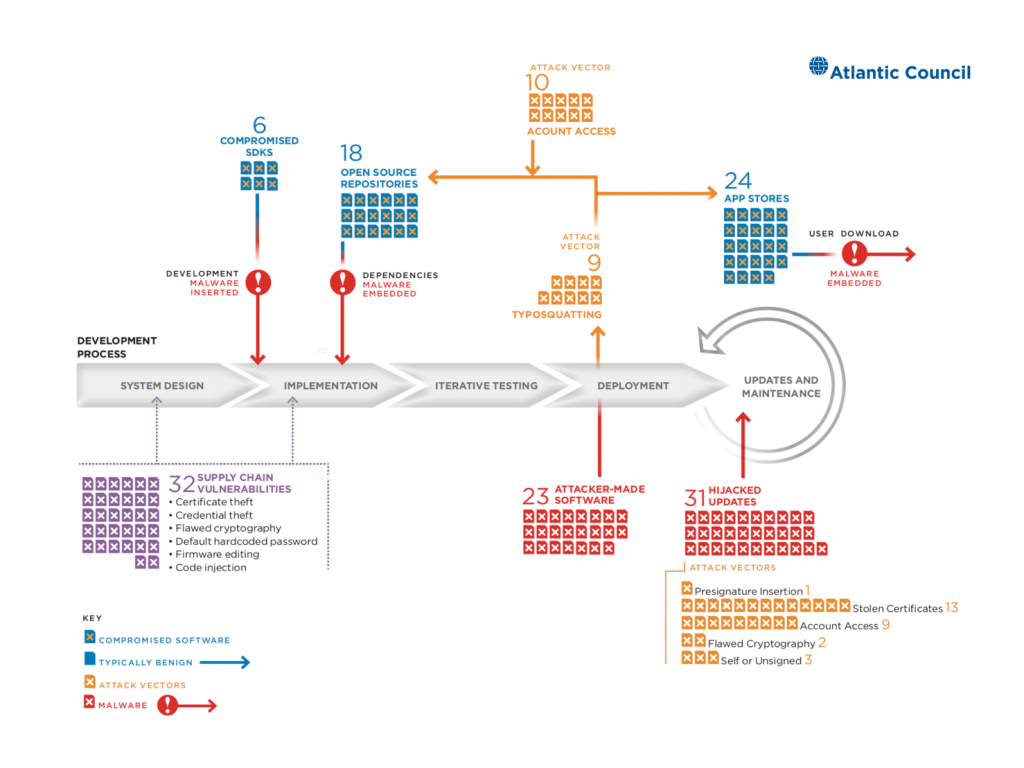
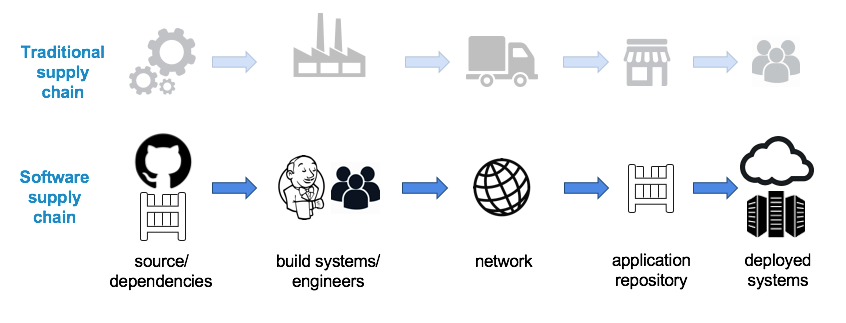
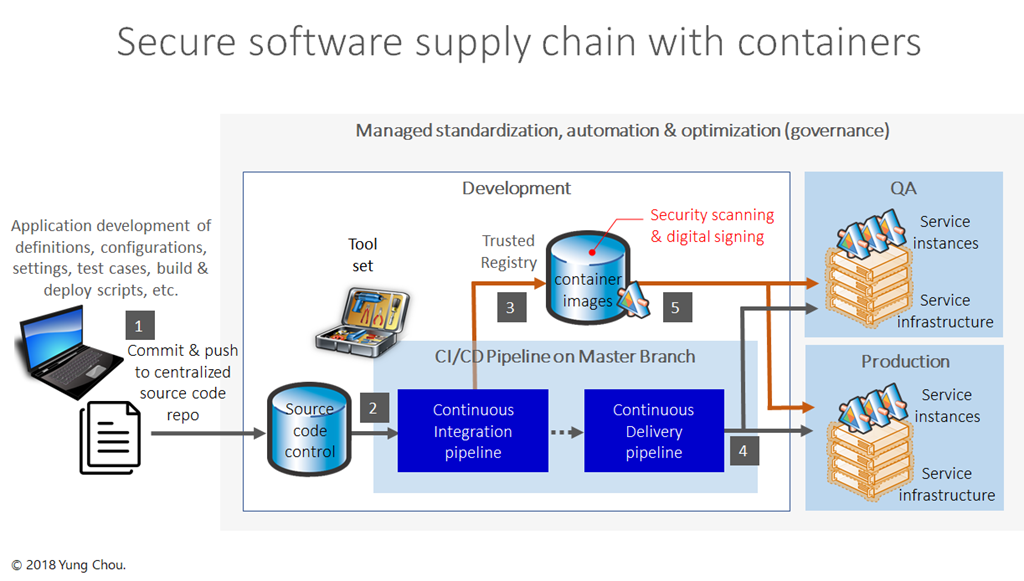
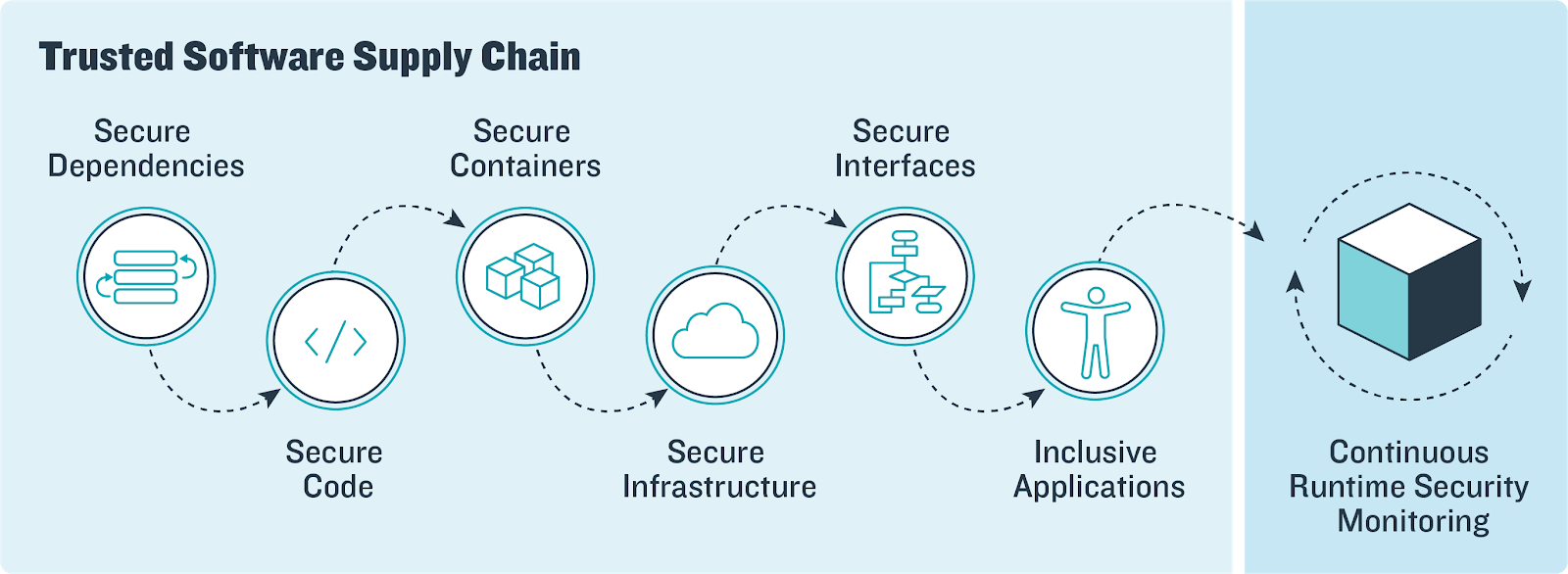
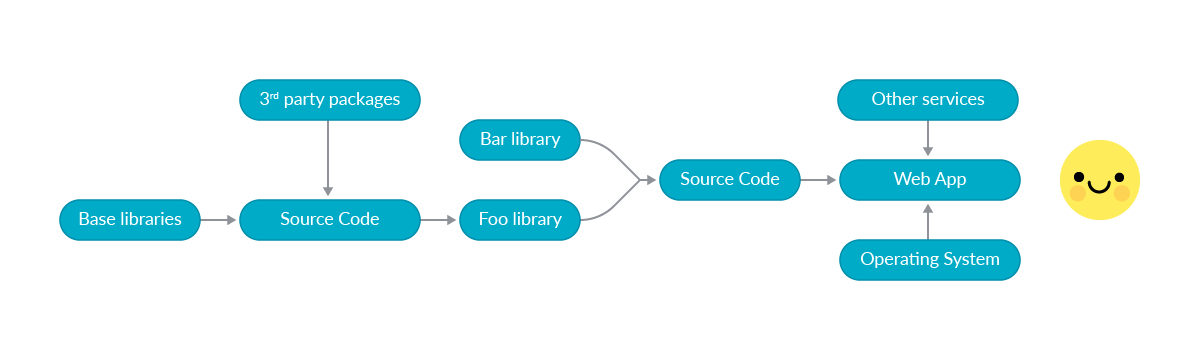
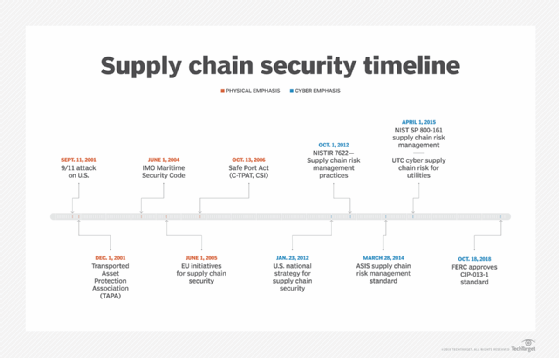
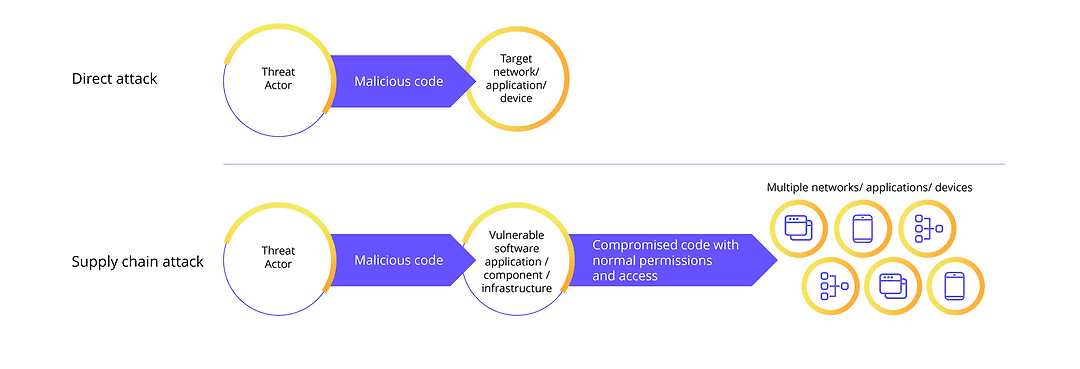
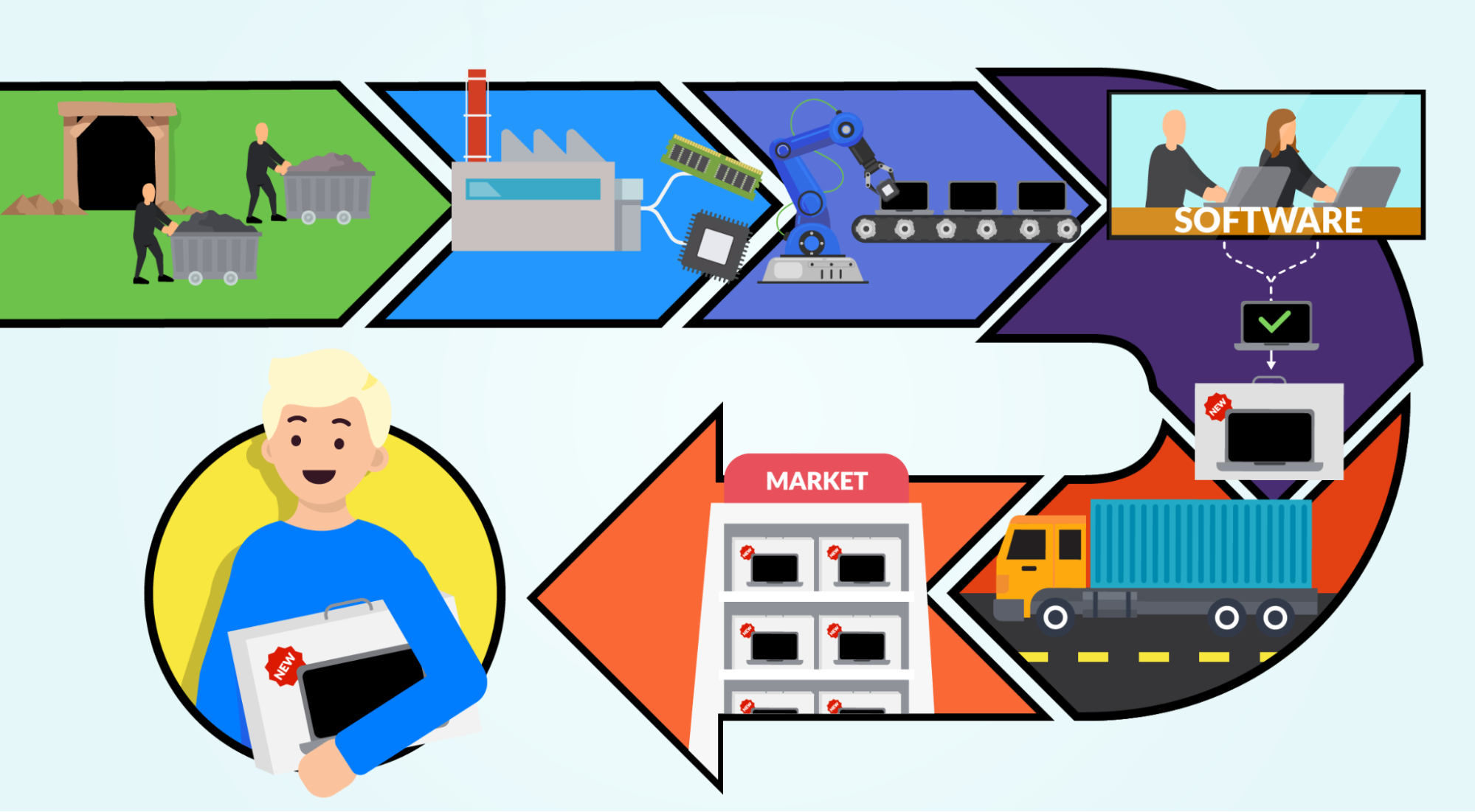
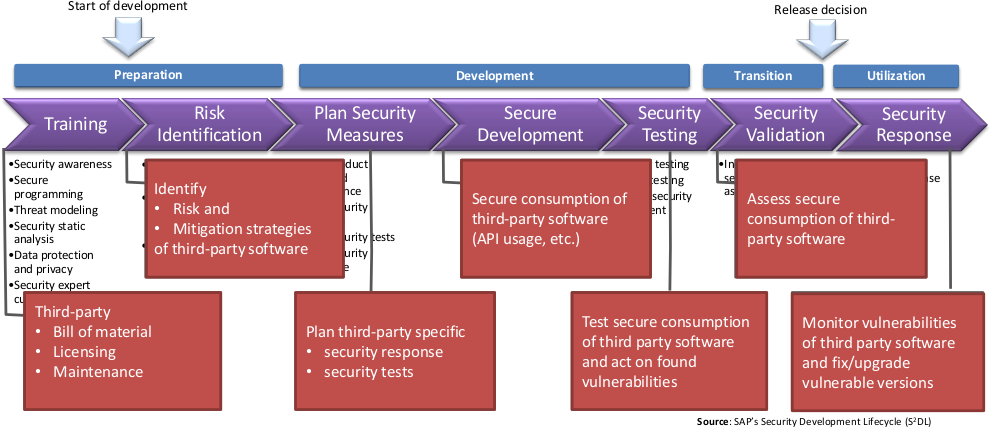
Secure at every step: What is software supply chain security and why does it matter? | The GitHub Blog

Download HD Secure Content Across The Software Supply Chain - Diagram Transparent PNG Image - NicePNG.com
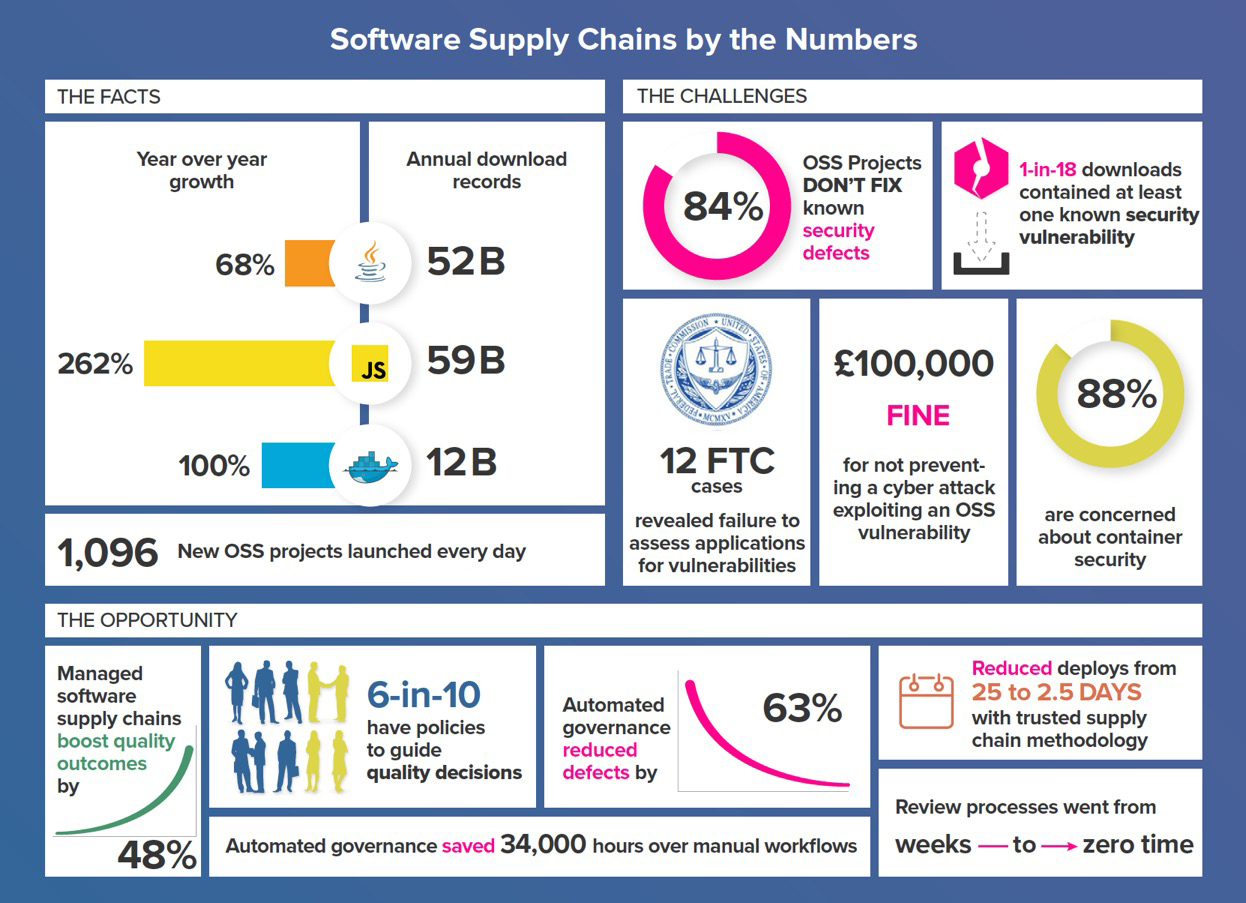
Sonatype 2017 State of the Software Supply Chain Report Reveals DevOps Practices Reduce Use of Defective Open Source Components by 63 Percent | Business Wire