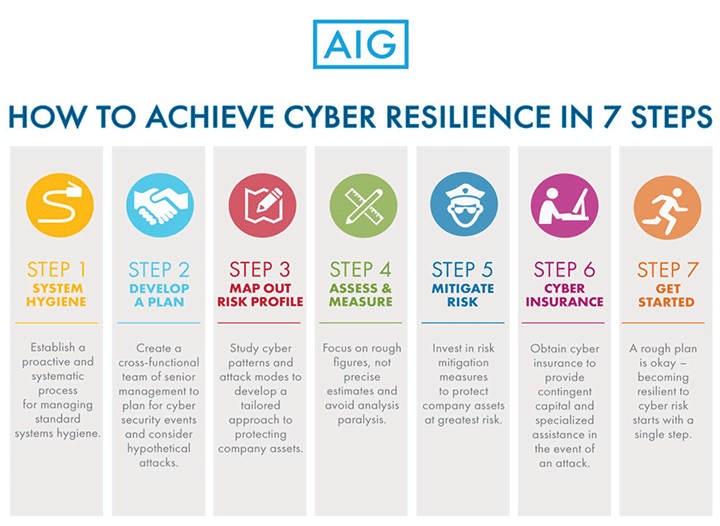
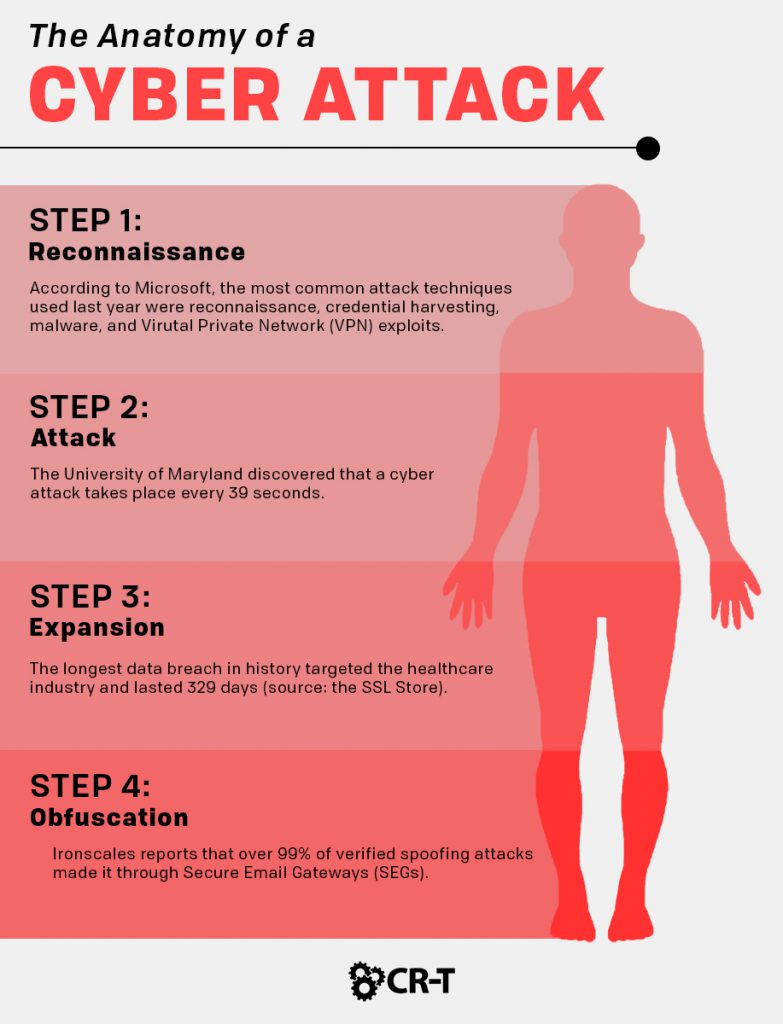
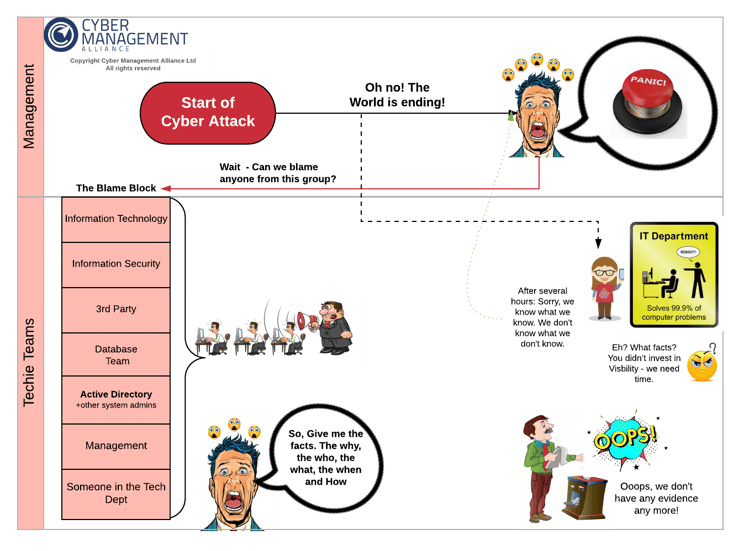
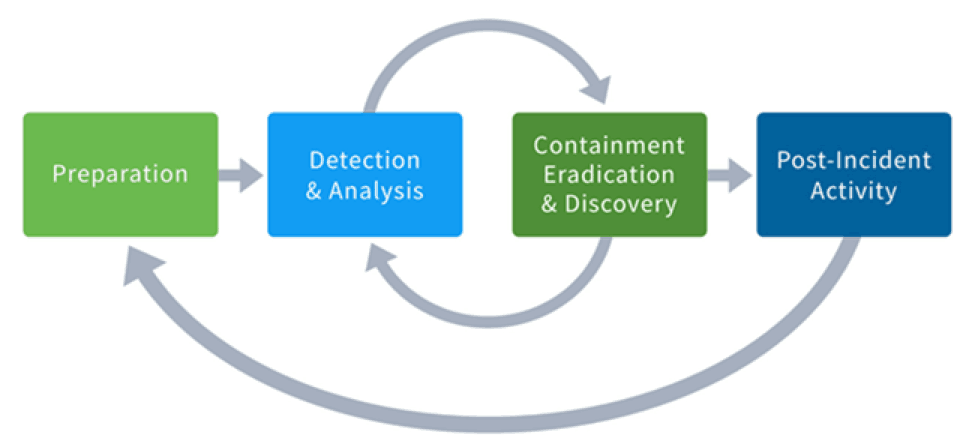
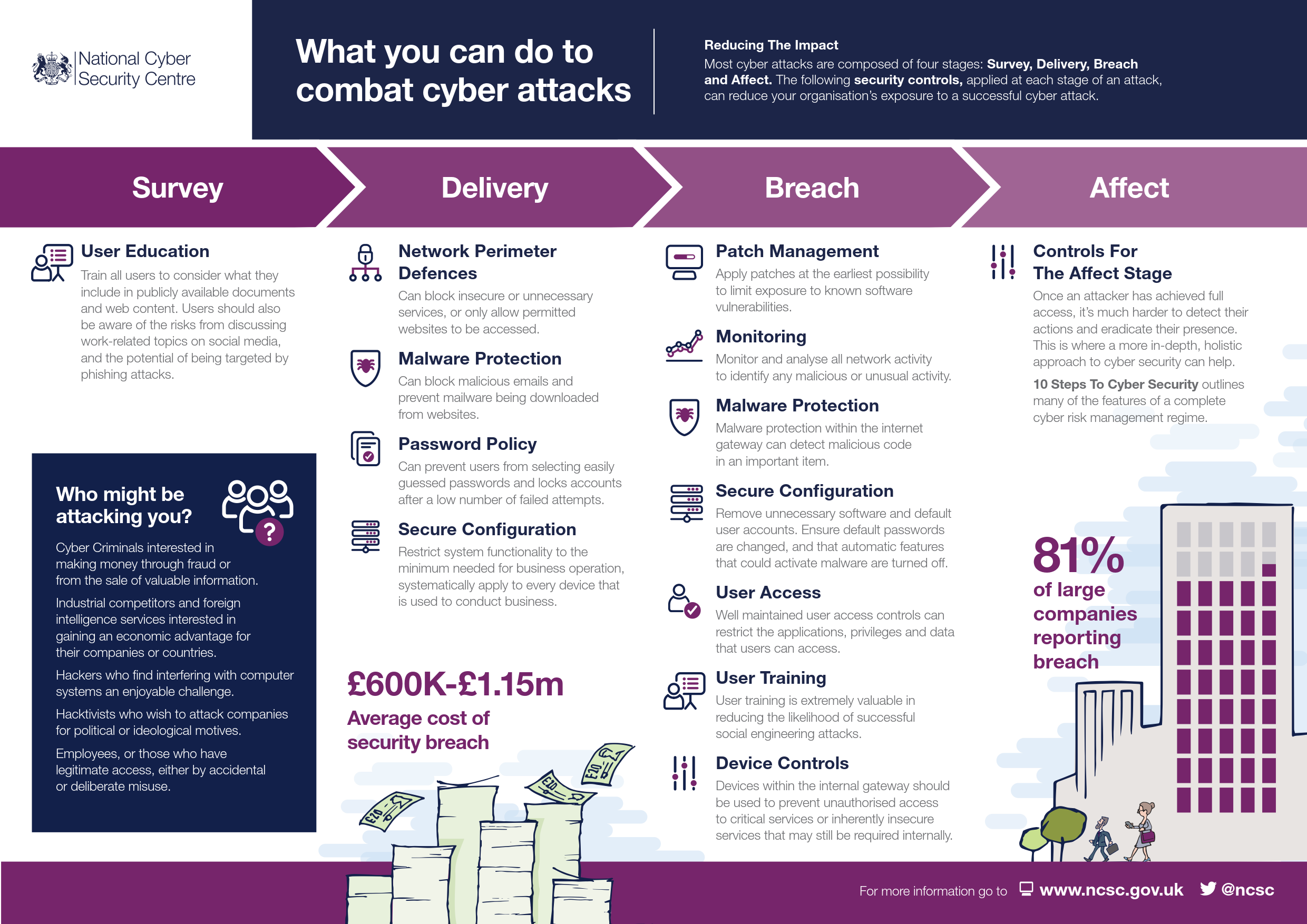
FIT Cybersecurity - Containment, eradication, and recovery are the three essential steps that every business should take after a cyberattack incident. Through these steps, we can isolate the attack and learn from

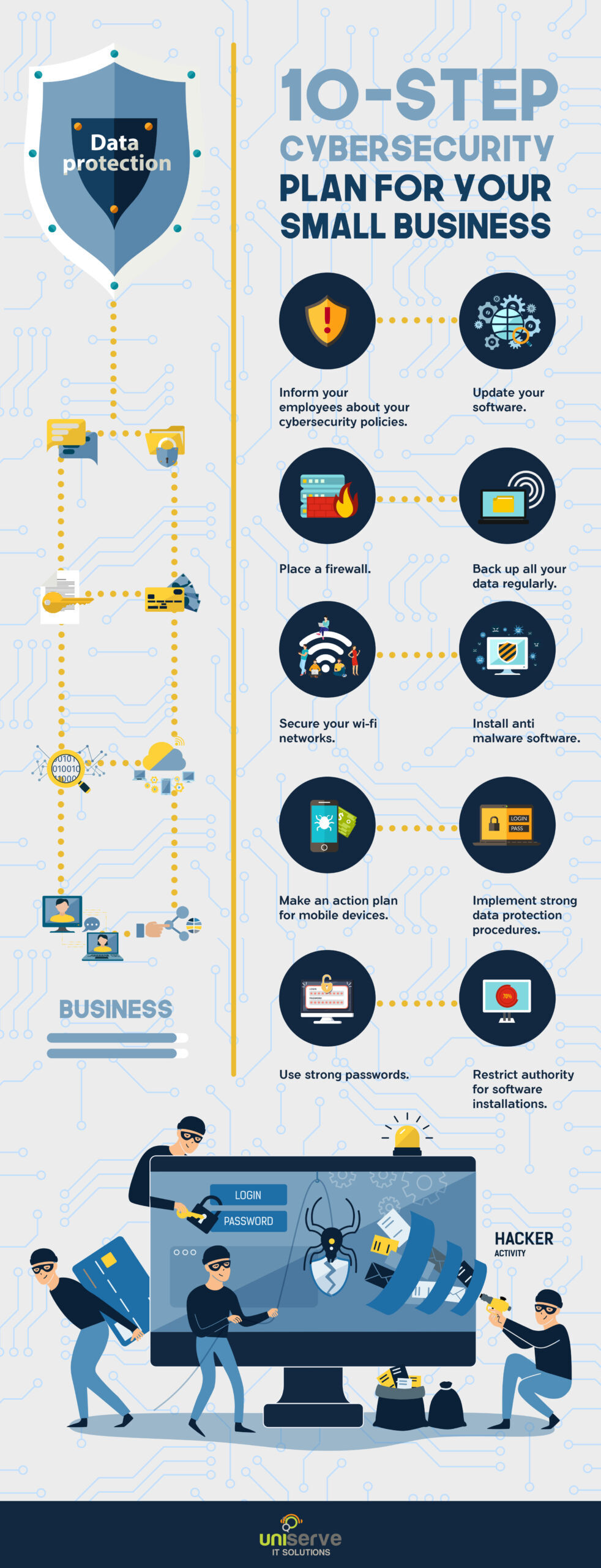
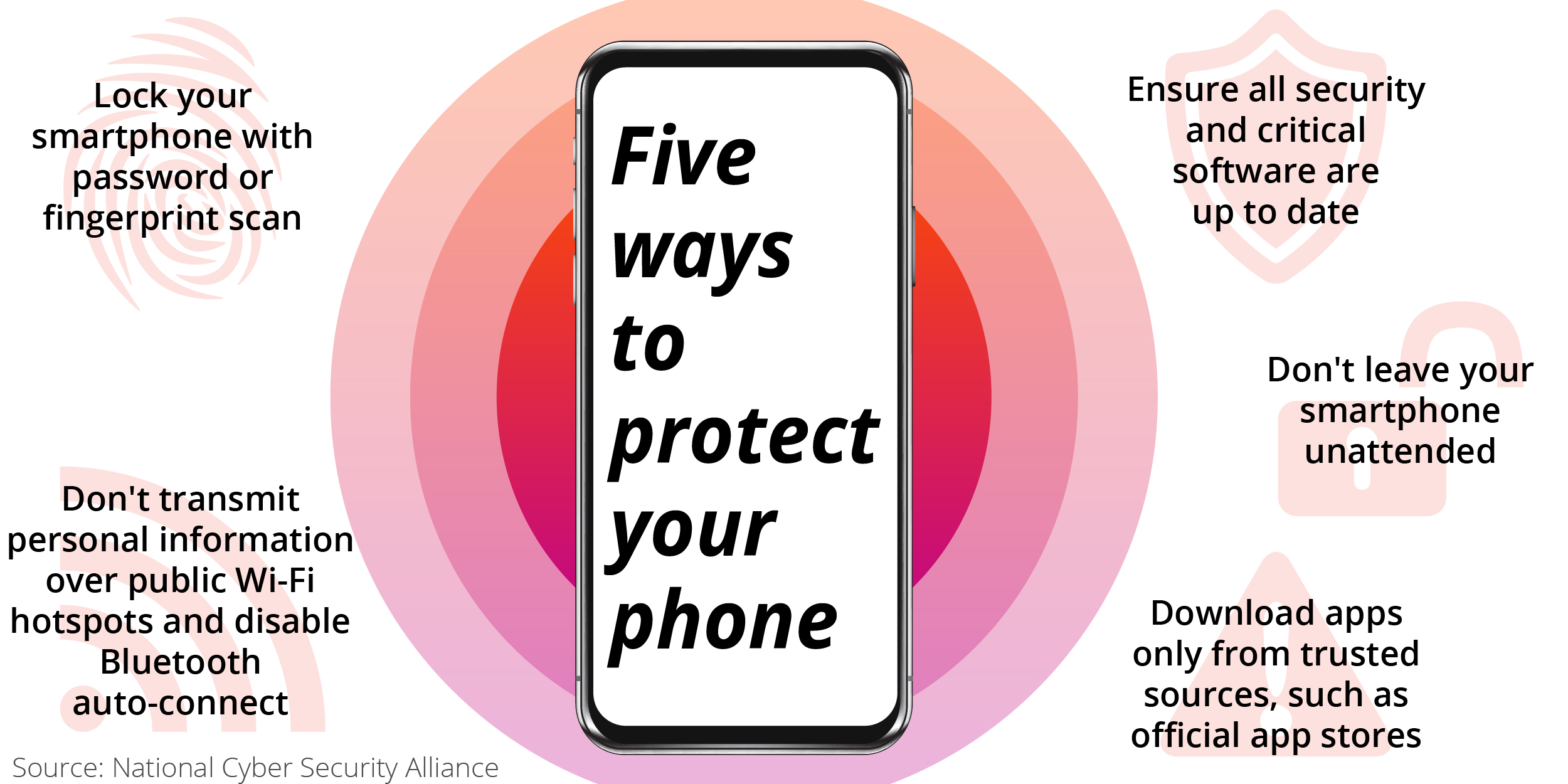
5 Actionable Steps To Secure Your Business From Cyber Attacks - Digital Brand Protection – FraudWatch